RAW Socket Packet Sniffer
This packet sniffer demonstrates how to capture IP packets under Windows by using RAW sockets. There are several methods to capture IP packets. The advantages of using the RAW socket method is clear. The program doesn't require any additional software or driver and only uses the existing operating system functionality. There are also some disadvantages of this method.
Disadvantages:
- Only packets of TCP, UDP and ICMP protocols can be captured.
- Ethernet headers can not be captured. As a result, there are no MAC-addresses in the records.
- IPv6 headers, which are essential to distinguish protocols, can also not be captured. But I solved this with a little trick.
- RAW socket sniffers requires an exception rule in the Windows firewall. The program adds this exception automatically to the Windows firewall at program start.
IP addresses
RAW sockets must be bound to local IP addresses. Select the local IP addresses to be bound to this packet sniffer.

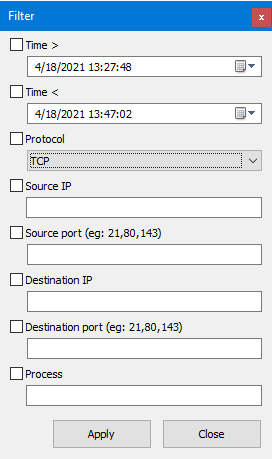
Filter
This program provides a filter function to display only specific packages.
Special features
- This program also records the path of the executable process that initiated the connection to which the respective packet belongs to.
- Captured packets are stored in a portable database so that it can be opened on another PC.
Note
This executable is stand-alone. That means, no installation is necessary. All settings will be saved in a INI-file in the same folder of the executable if the folder is writable. There is also a prompt to create a database for captured packets at the first start of the program. The recording process must also be started manually. Just click "Record" in the main menu and then "Start".
Download:
- Windows 32-bit: RawSocketPacketSniffer32.exe
- Windows 64-bit: RawSocketPacketSniffer64.exe
Change log:
- Version 1.0.0.0: Initial version
Categories: Windows Tools Internet


 Home
Home Posts
Posts Categories
Categories Archive
Archive Contact
Contact

